
Disclaimers: This is an OpEd by Marcus Dean Adams. Any opinions stated here do not necessarily reflect the stance of Appalachia Insider or any of its subsidiaries or affiliates. This post was originally made to my personal WordPress blog. That copy of it is going to be a sort of “living document” that I revisit from time to time as facts change, technology progresses, or as I learn more. I’m posting this copy to help spread awareness to folks I think may benefit from it, but this copy may not get updated when the original does. If you’d like to see the latest version of this article on my personal blog, you can see that version of it here:
During a podcast I did a while back I was asked how to tell if your device has been compromised. Last night somebody I follow posted on Mastodon asking for input on the same issue, or how somebody could tell if they’re being stalked.
With all that in mind I thought I would do what I can to provide information on ways to tell if your device has been compromised, or if somebody (a spy, an abusive spouse/lover, etc.) has installed stalkerware on it without your knowledge, and what to do about it. I use and only personally have access to Android devices, so if you are an iPhone user, consider checking out other resources, like “The New Oil” that Nate, in the screenshot above, runs. Keep in mind that your device’s UI may look slightly different than mine, depending on the Android version and whether your device manufacturer has included their own UI.
First it’s important to define a few terms. A device being “compromised” can mean a lot of things; but generally it means that for some reason the device is running software that’s causing it do things it shouldn’t be doing, often to steal personal information about you, to participate in a botnet or other questionable activities, without your direct knowledge or consent. Stalkerware is exactly what it sounds like, software that is used to stalk you. There are legitimate reasons to use many of the products that can be considered “stalkerware”; such as parents wanting to keep track of their young children, families wanting to keep track of each other on trips, or when I misplace my phone, being able to use my wife’s phone to check the location of mine to make sure I didn’t leave it at work or something. However, these legitimate tools are also often used by abusive partners to control and track their victims. They might want to be able to read your private messages, keep track of your location, listen in on your calls or do various other things to invade your privacy and keep you under their control. So, the question is how do you know if this is happening? Whether it’s a virus or a stalker, here are some things to check to see if your device could be compromised.
How to Know
Battery Consumption
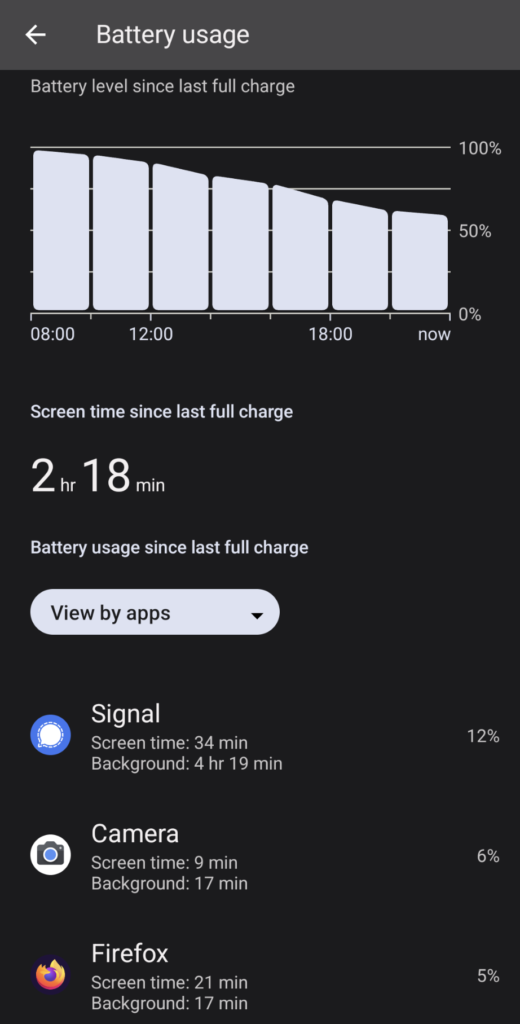
If a malicious app is doing a lot of stuff in the background, the first thing you might notice is that your battery doesn’t last as long as it used to. Some degradation in the life of your battery is normal as your device ages, but if you’ve noticed an unusual change in how long it lasts, or have noticed your phone getting hot to the touch when you aren’t doing anything, this could be a sign of something going on in the background without your permission.
The good news is that Android lets us see which apps or processes are the biggest drains on our battery. Just go to:
Settings -> Battery -> Battery Usage
Scroll down a little and it’ll show you, in order, which apps have taken the biggest chunks out of your battery since your last full charge. If you see something listed here that you don’t recognize, it could indicate that somebody has installed something on your device without your permission.
Location Permissions
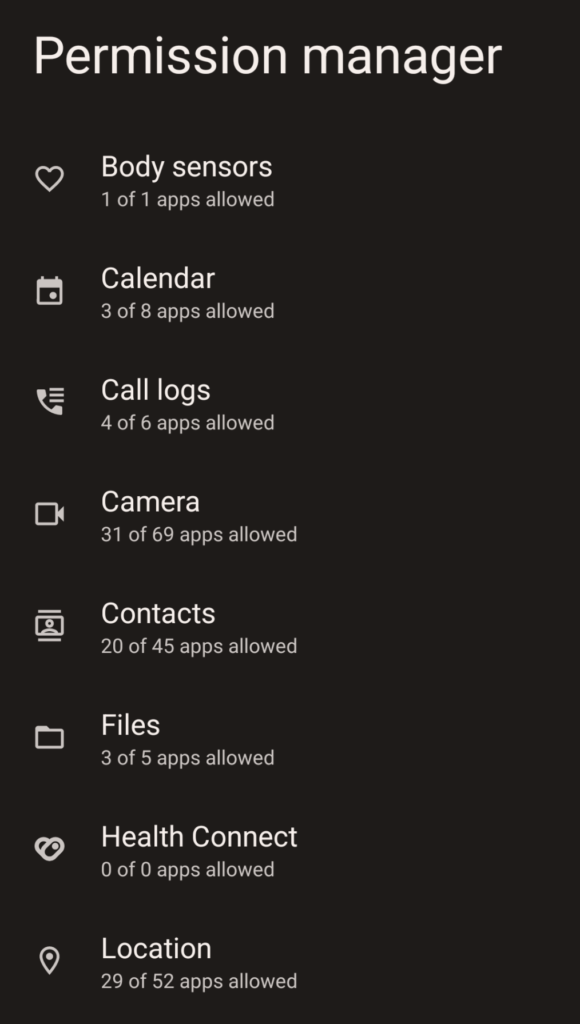
Your device keeps track of what apps have access to various permissions and when they access it. If you go to:
Settings -> Security & Privacy -> Privacy -> Permission Manager
You’ll see a list of the various permissions your device can grant to applications.
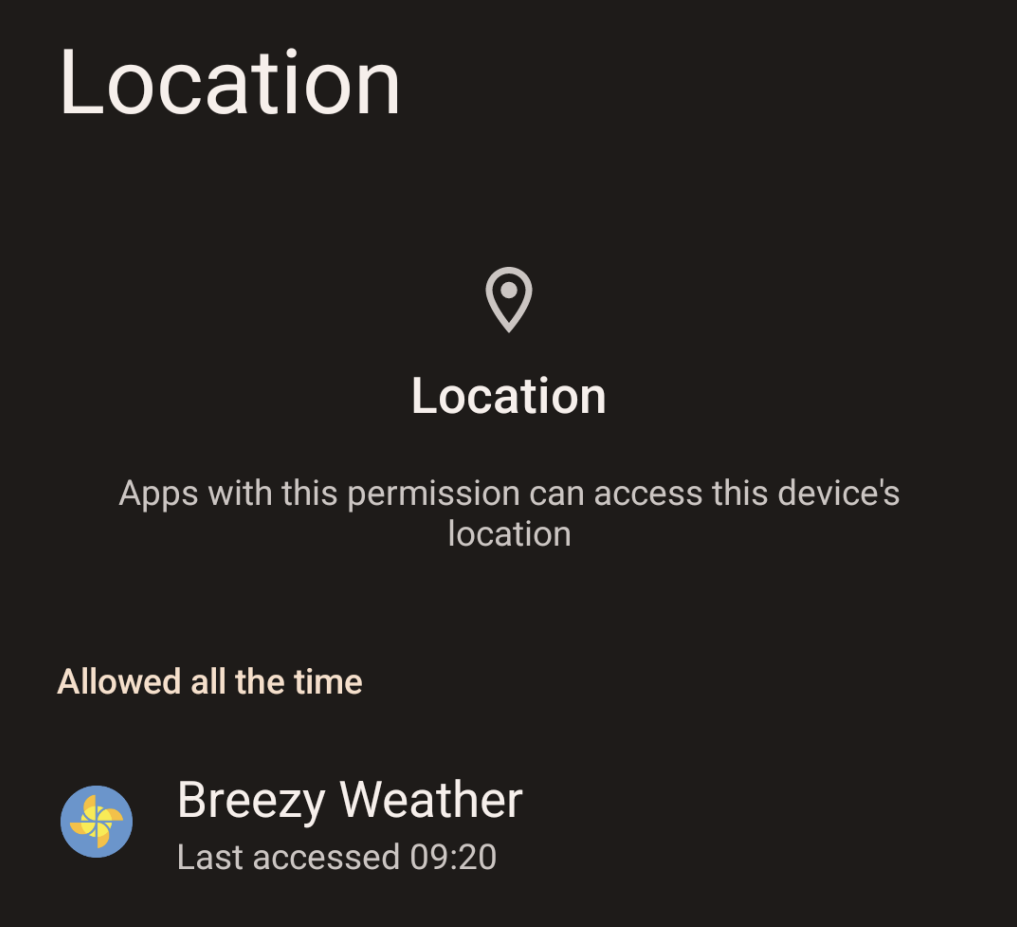
Click a permission you want to review, such as location, and it will show you a list of apps that have been granted that permission. You can click an app to see the last time that particular app requested something from that permission.
Device Administrator Apps
Some applications can be set as “Device Administrator” apps. These applications essentially have the highest level of access a user can grant them from within Android. They can set policies and controls that apply to both the user and other applications on the device. They can unilaterally lock a device, wipe its internal storage and perform other actions that normal apps can’t do. Enterprises can use this to enforce password policies, restrict app usage or installation and other things on employee devices. There are some legitimate reasons to give an app this permission. For example, the app I use to stop my kids from changing settings on their phones requires “Device admin” privileges.
However, this privilege can be abused. Someone can install an app they want to use to stalk or control you and give it “Device admin” privileges, meaning they can’t just see what you do on your device, but can control your access to your own device. To check which apps have this permission go:
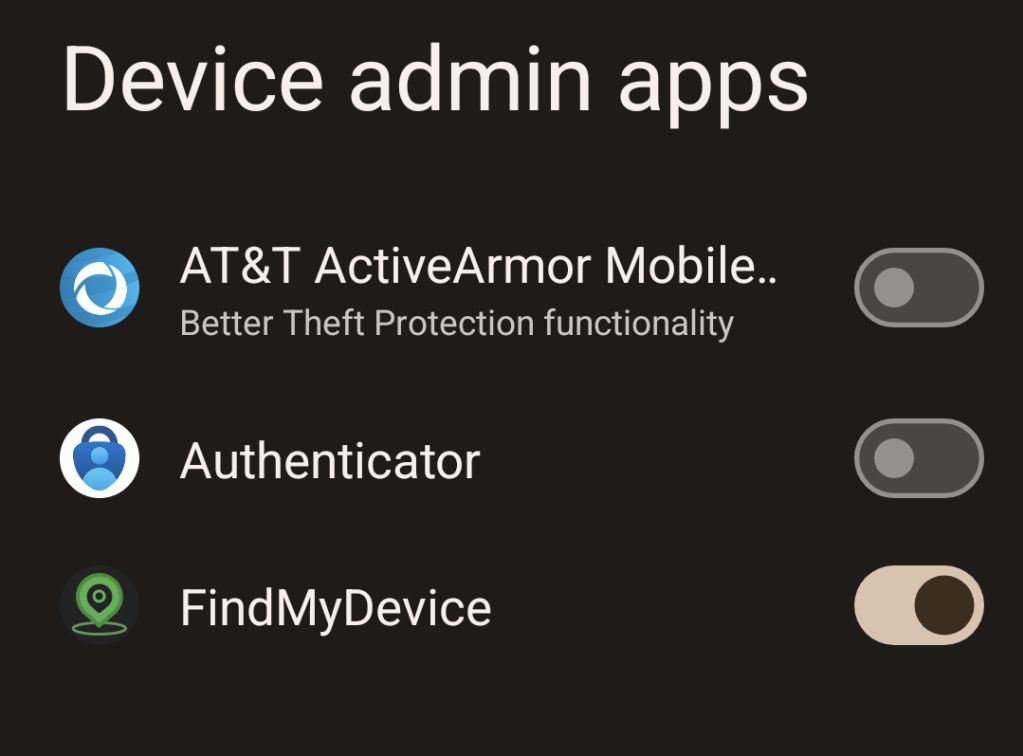
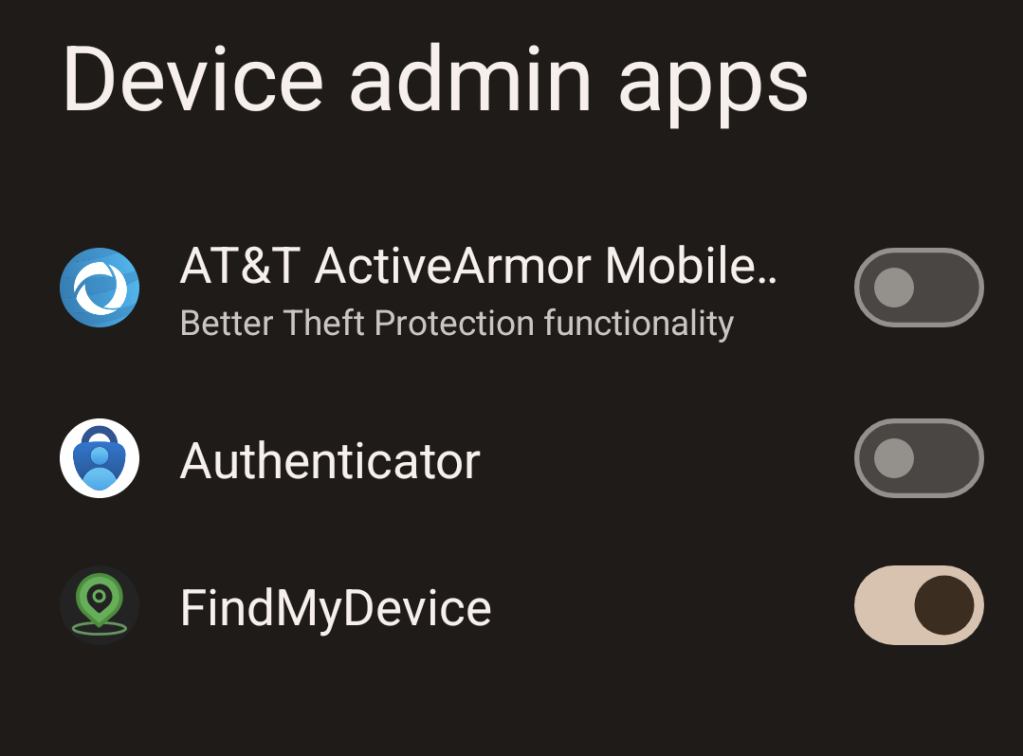
Settings -> Security & Privacy -> More Security & Privacy -> Device admin apps
A list of apps that can be set as device admin will be listed, and any of them that are active will have their toggle turned on. In this example you can see that I have granted that permission to the “FindMyDevice” app, which I’ll discuss in the “Stalkerware” portion of this post.
Accessibility Access
Another permission that can be abused is your “Accessibility” settings. Sometimes this can be useful. For example, I use the “KDE Connect” app with this permission so that when I’m home on my laptop, my phone can make its notifications and messages available on my laptop. I can use KDE connect to browse files, messages, etc. on my device wirelessly. I can even use KDE Connect in reverse to control my PC, using the KDE Connect app as a mouse or keyboard for my PC. But, I specifically installed this app, and so consented to giving it this access. But this permission can also be abused by malware or stalkerware to give it access to things it shouldn’t have access to.
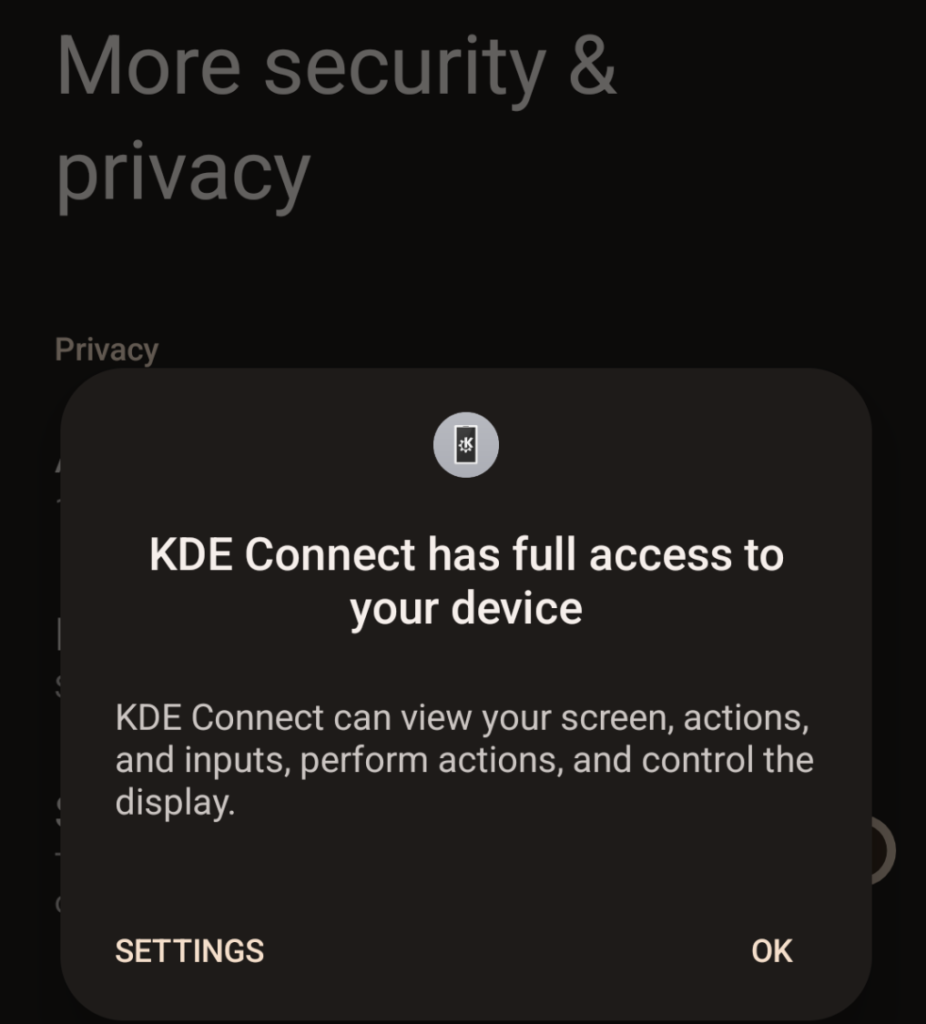
To check what apps have this permission go:
Settings -> Privacy & Security -> More Privacy & Security -> Accessibility Usage
Accounts
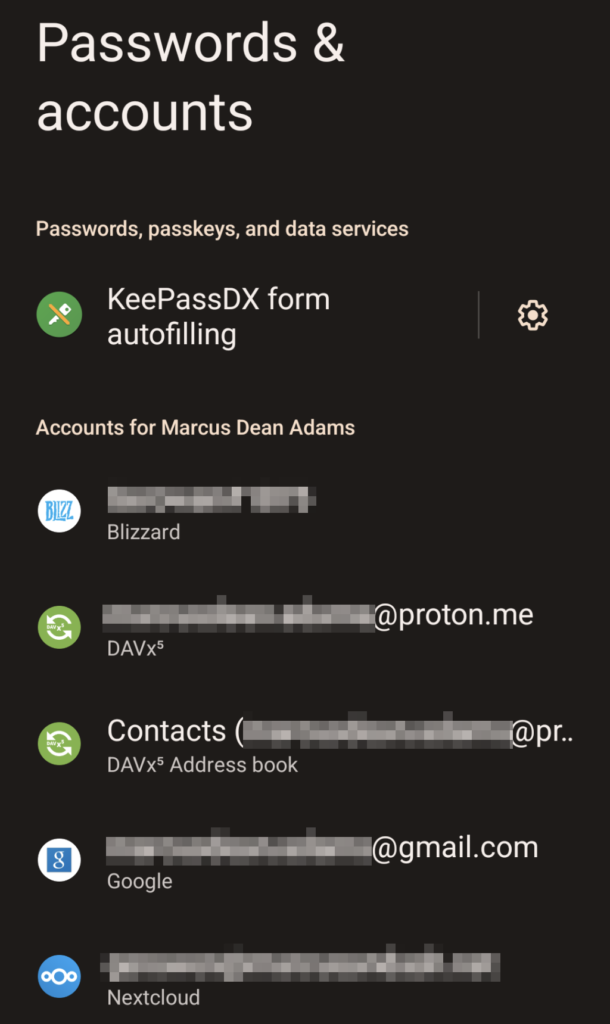
One other way someone could use or track your device is by just adding their own account to it; say their Google account for location tracking. You can verify which accounts have been saved to your device by going to:
Settings -> Passwords & Accounts
Review what’s in here and make sure nothing unusual or suspicious is listed.
Special App Access
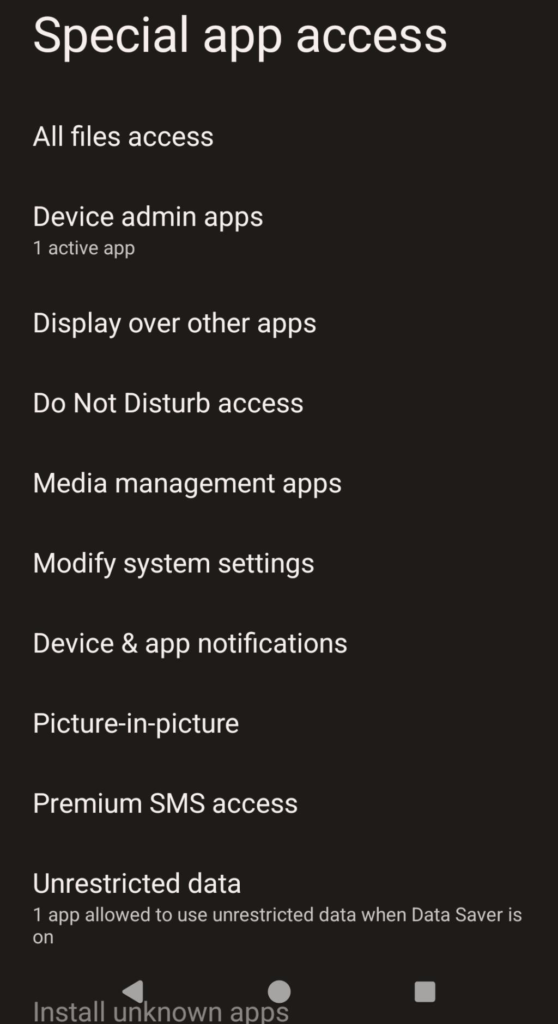
Go to:
Settings -> Apps -> Special App Access
This is a more unified interface for listing “special” access privilegs that various apps on your device may have. This will contain things like “Device admin apps” that I already mentioned, but it also has several more categories like “Modify system settings” and “All files access” that you should review to make sure nothing unexpected is listed in any of these categories.
Unknown Applications
Review what apps are installed on your device. Just go:
Settings -> Apps -> See all apps
And go down the list of what’s installed on your phone to make sure nothing unexpected has been installed on your device.
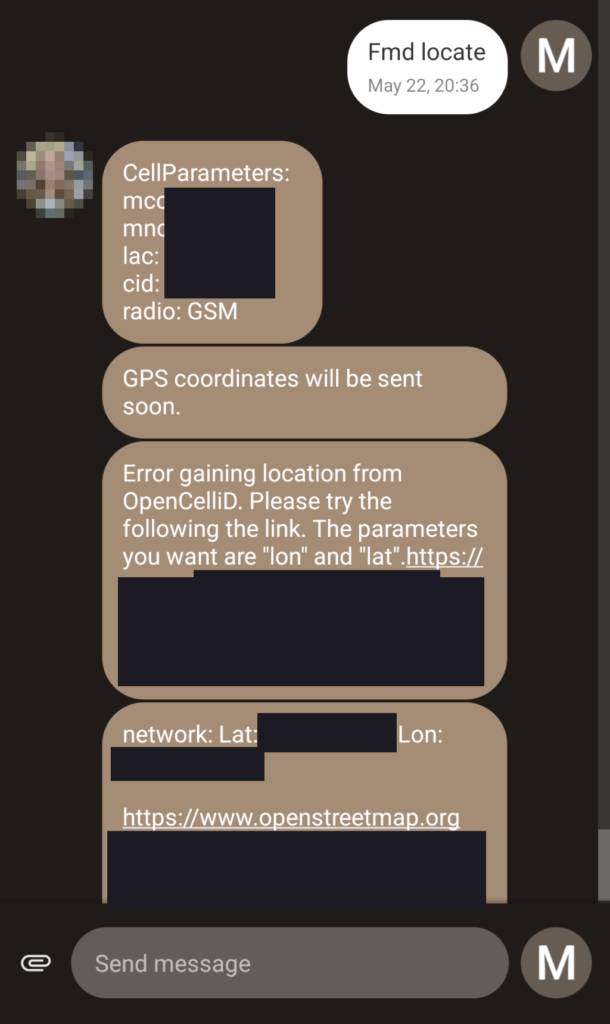
Odd or Unexpected Text Messages or Notifications
Some malicious applications can use things like SMS as a means of “C2”, or “Command and Control”. For example, the “FindMyDevice” app that I and my family use to keep track of each other can read messages and, if a command is received via SMS from an approved number, perform various actions; such as reply with our location, make the phone ring, wipe the whole device, etc. However, if an app like this were installed without your permission, strange or indecipherable messages might be a sure sign that somebody is using it to track or control you. Watch for notifications from apps you didn’t install or don’t recognize too, or that contain odd or cryptic message text.
Antivirus Warnings
There are a variety of antivirus solutions for Android. If you’re using one, like Bitdefender or AT&T’s “ActiveArmor” and it regularly finds infected files on your device, that could be a sign of something going on that shouldn’t be.
What to Do
Safe Mode
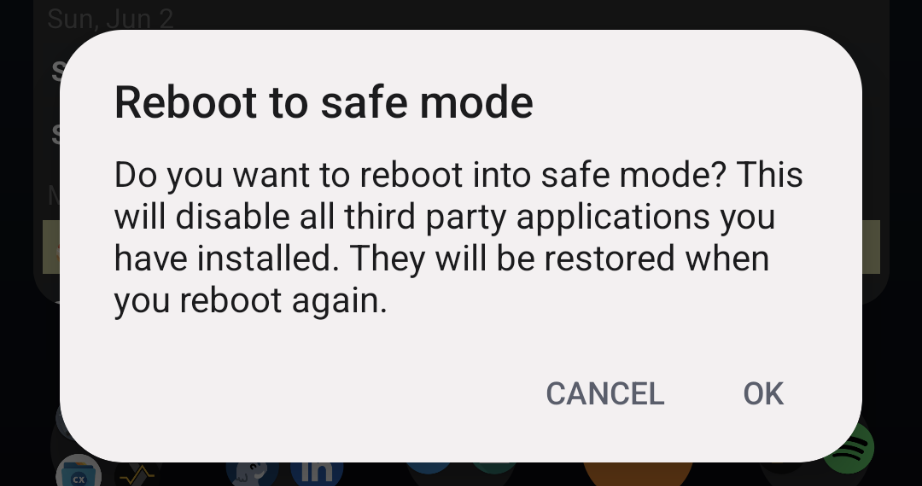
It’s important to know that sometimes you can’t perform certain actions that I’ll describe below without booting into safe mode. Sometimes an app will prevent you from uninstalling it unless you’re in safe mode, or you can’t modify certain settings or files unless you’re in safe mode. The method for entering safe mode varies depending on your device vendor and the version of Android you’re running. However, on my Google Pixel 6a running CalyxOS, you can enter safe mode by:
- Press and hold the power button until you get the menu asking whether you want to shut down, restart, etc.
- Touch and hold the “Restart” option. You should get prompted to reboot into safe mode.
Antivirus
There are a variety of antivirus solutions available for Android. Some of them can come from your carrier. For example, AT&T has an app called “ActiveArmor” that will scan your device for known malware. It also lets you block spam calls and text messages, send unknown callers directly to voicemail, etc. BitDefender, Malwarebytes and other antivirus vendors also have mobile versions of their antivirus products. CalyxOS, the third party Android ROM that I use, ships “Hypatia”, a free open source antivirus, by default. It is also available in the third party “F-Droid” app store, if you would like to try it out.
Uninstall Offending Applications
Obviously if, while investigating you discover a malicious application has been installed, you should uninstall it. If the app has been granted “device admin” privileges, you may have to deactivate that permission before you can uninstall it. You may get prompted about this when you try to uninstall it, but if you don’t, you may have to do it manually. Just go to:
Settings -> Security & Privacy -> More Security & Privacy -> Device admin apps
And turn off the toggle for the app. Then you should be able to uninstall it.
Use a Firewall to Limit Network Access to Offensive Applications
If for whatever reason you can’t uninstall a malicious application on your device, or if you need or want an app but don’t necessarily trust it not to do shady stuff in the background, you can use a firewall app to limit or block an app’s access to the internet.
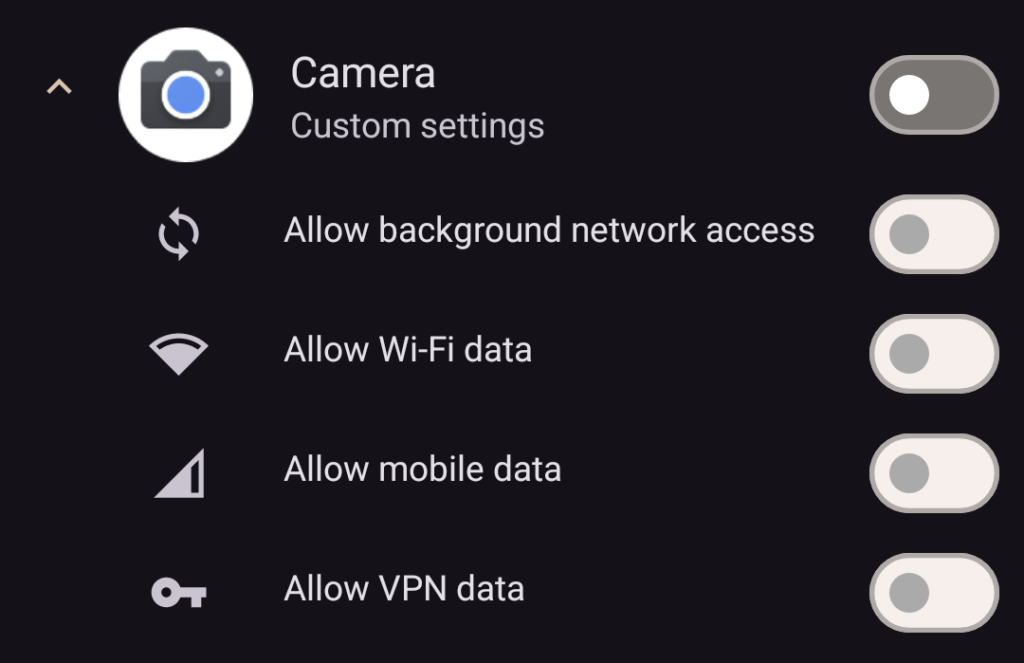
As a CalyxOS user my phone came with the “Datura” firewall pre-installed that lets me control what, if any internet access applications on my phone have. For example, I like Google’s camera app, so even though I use CalyxOS, I installed their Pixel camera app. But, I don’t trust Google not to be shady, so I used the firewall to block that app’s internet access.
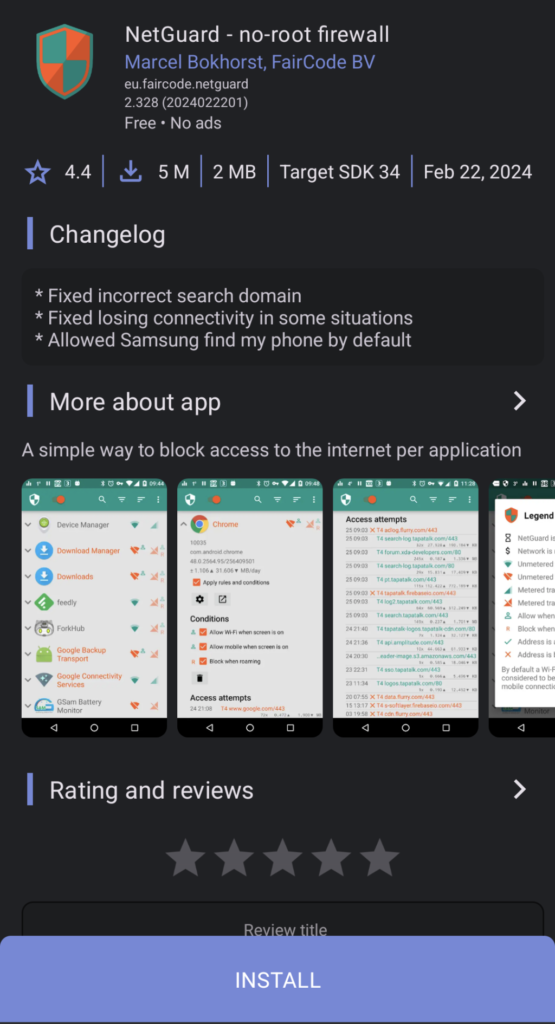
For the majority of you who aren’t on CalyxOS, there are firewall apps in the Google Play store. One in particular that seems to get a lot of positive reviews is called “NetGuard”. It works by essentially creating a fake VPN connection to itself, therefore forcing all apps to route themselves thru that app before they get to the internet. This allows NetGuard to control which apps do or do not have internet access.
One thing to remember however is that an internet firewall may not block things like SMS messages or calls relayed by your cell provider. So if an app like FMD (FindMyDevice) was installed without your permission, and responds to SMS messages, it doesn’t need internet access to function. Like most things, an application firewall is one tool in your toolbox, but it won’t be a magic bullet for all scenarios.
Wipe or Replace the Device
If all else fails, say for example the phone won’t let you revoke “device admin” privileges, or uninstall a malicious app, the one certain way to remove the infection is to either perform a factory reset of the device, or replace it altogether.
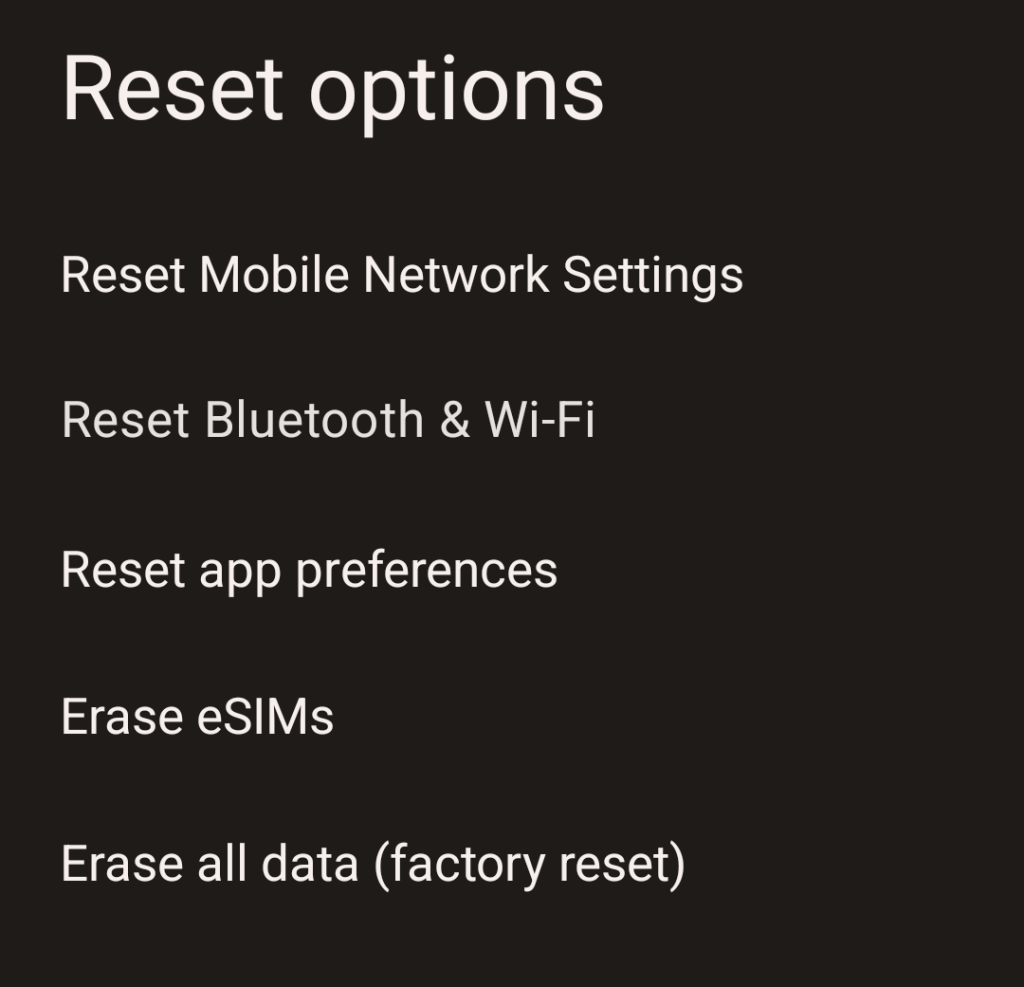
To perform a factory reset of an Android device go to:
Settings -> System -> Reset Options
Then click “Erase all data (factory reset)”. This should initiate the process of doing exactly what it says; wiping all of your data and restoring the device to its factory condition.
Note however, that if you got the device from your abuser or stalker, or if you have specifically been targeted by a determined threat actor, and it is not running an original factory version of Android, it is possible that this may not remove the infection. It’s possible that the operating system itself may be the source of the malicious apps and/or infection. The FBI once set up a fake company called “Anom” that sold “encrypted” phones to drug dealers. The devices ran a custom version of Android that, rather than “encrypting” their messages, sent copies of them back to the FBI. Compromised devices like this still exist and can be bought online, so if you suspect this may apply to you, your best bet would be to just perform the factory reset to remove any existing personal information, like photos, and then replace the device altogether. One way to check if you’re running a third party ROM, though this isn’t definitive, is to go to:
Settings -> About phone
And examine what you see in there. Since my phone runs CalyxOS, besides the normal information about Android, you can see that it lists the version of CalyxOS I’m using. However, you can only use this to confirm a device “is” running something else. You cannot use it to confirm that a device “isn’t” running a compromised operating system. The information here could obviously be forged in order to fool people who care enough to look.
Prevention
There’s an old saying that an ounce of prevention is worth a pound of cure. Even if you don’t think your device has been compromised, it’s important to take reasonable precautions to protect it and yourself. Preventing problems in the first place is usually easier than fixing them after they happen.
- Use a good password on your device, and don’t share it with anybody you don’t 100% trust, such as your spouse, assuming you are in a trusting relationship and they aren’t the one you’re trying to protect yourself from.
- Use a firewall app, such as Datura or NetGuard (mentioned above) to manage which applications can access the internet and when.
- Don’t give apps more permissions than they reasonably need, and review those permissions occasionally to make sure you haven’t granted something access that it either shouldn’t have, or doesn’t need any more. If you aren’t geo-tagging your photos, your camera app doesn’t need access to your location. That mobile game you installed most likely does not need access to your photo gallery, etc. Don’t be afraid of hitting the “Deny” button when an app requests a permission.
- Keep your device and apps up to date. The method differs by manufacturer, but if you go to:
Settings -> System
You should see various settings related to checking for system updates. - Use a reputable antivirus on your device. Google does a decent job, but they and Apple both regularly have malicious apps sneak their way onto the app store and sometimes, a device can be compromised remotely with you even installing an app.
- Use an ad blocker like uBlock Origin in your mobile web browser, or use a browser that blocks ads and trackers by default like Brave or Vivaldi. Even the FBI recommends that folks use an ad blocker because of the risk of drive-by “malvertising” where simply visiting a website can cause your browser to load an ad with malicious code in it that may then be able to comrpomise your device.
- Don’t install applications you don’t need. Many services work just fine in a web browser. For example, the majority of Facebook’s functionality is available on their mobile web page, so if you don’t use it to go live, you probably don’t need the app, just visit the website in your phone’s browser.
Conclusion
Devices can get compromised in a number of ways. You can be in an abusive relationship with somebody who put stalkerware on your phone so they can track your movement or control what you can or can’t do on your device. You might be a reporter who is being targeted for speaking out against those in power. You might be a leader of some kind being targeted by espionage agencies. Or you might just be a regular person who clicked a bad link and unknowingly contracted some malware. Whatever the reason, the important thing is to identify the threat and get rid of it.
It’s also important to remember that while I am a big proponent of apps like Signal for secure communication, they are not a magic bullet. The only thing Signal can guarantee is the security of your messages while in transit. Signal encrypts your messages “end-to-end”. Your phone is one of those ends, and the messages have to be decrypted on either end so they can be read. So if you have malware or stalkerware running on your device, or if the person you’re talking to has their device compromised, it’s possible for bad actors to read your messages no matter what messaging service you’re using. So if you know you are in a situation where you suspect your device has been compromised, it’s important that you take steps to remove the infection or replace the device, because just installing Signal isn’t enough if your device itself is otherwise compromised.
Our phones are basically an extension of ourselves. We do everything on them; from chatting with friends to banking, so it’s important we take their security seriously. Hopefully the steps I’ve outlined here will help you keep a good eye on your device so that you can protect yourself and maybe even others around you.
Donate
Articles like this take time and effort. If you’ve found anything here helpful, useful or informative, a donation to compensate me for my effort would be sincerely appreciated. There are multiple ways you can do so including:
PayPal: https://paypal.me/gerowen
LiberaPay: https://liberapay.com/gerowen
Bitcoin (BTC):
bc1q86c5j7wvf6cw78tf8x3szxy5gnxg4gj8mw4sy2

Monero (XMR):
42ho3m9tJsobZwQDsFTk92ENdWAYk2zL8Qp42m7pKmfWE7jzei7Fwrs87MMXUTCVifjZZiStt3E7c5tmYa9qNxAf3MbY7rD

