An OpEd by Marcus Adams. An overview of “Incognito Mode” or “Private Browsing” features in web browsers, filtering out the hype to discuss their limitations and what they’re actually useful for. Any personal opinions stated here do not necessarily reflect the views of Appalachian Insider (Formerly Magoffin News Network). More information about the author can be found at the bottom.

Online privacy and security is a process. It’s a process that, depending on the situation, may involve the use of a multitude of tools, technologies and processes to keep yourself as safe as reasonably possible. One of those tools that has been added in recent years is “Incognito” or “Private” modes in most web browsers.
“Incognito” or “private” mode in your browser is a valuable tool in your arsenal. Something that you can use to help protect yourself, but it’s not entirely what it might seem to be on the surface, or what some companies have marketed it as. The name is a little misleading. Google recently agreed to settle a $5 billion dollar lawsuit alleging that it spied on users using the “incognito” mode built into the Chrome browser, and other similar modes/features in other browsers.
Source: https://www.npr.org/2023/12/30/1222268415/google-settles-5-billion-privacy-lawsuit

That’s not to say that incognito or private modes aren’t useful, but it’s important to understand what they really are and what their limitations are, so that you aren’t lulled into a false sense of security. So first, here’s some things that these modes won’t do:
- Hide your identity, IP address or location from websites you visit
- Hide your browsing activity from your internet service provider
- Protect you from viruses or other malware that might be present on shady websites
- Prevent tracking by your browser vendor

What private browsing modes “do” do however, is create an essentially ephemeral browsing session where none of your normal browsing cookies will be valid and, once the window is closed, the cookies and browsing history from that private session will be erased. This can be useful for a variety of reasons. For example, when I help friends or family do their taxes once a year, I usually use a private browsing window to do it. That prevents any of my information from getting automatically filled in by accident, and it also prevents any form entries I make in that session from getting committed or saved to my personal session. It basically makes sure that the only thing going on in that window is that task, and once I close it, none of the data entered in that window can cross contaminate with my personal browsing session.
Private browsing can also be useful if you share a computer with somebody and need to protect access to your accounts, browser and search history, etc. from others who may have physical access to the same machine and browser. For example, if you’re away from home and want to use a public device, such as at an internet cafe, to check your email or social media account, doing so in a private window will prevent others from being able to access that account after you close the window (assuming the computer is free of malware). This might also be valuable if you are a domestic violence victim where you may use a shared computer to seek help and don’t want your abuser to be able to view your browsing or search history.
Private browsing can protect websites from seeing cookies related to your regular browsing sessions. Cookies are small files that store information about sites you’ve used. When you return to Facebook and don’t have to sign back in, that’s because a cookie was used to facilitate that. Some websites will try to take a peek at what cookies exist on your system in order to collect information about you and the other sites you’ve visited. If you’ve ever done a search for an item, then seen an ad for it on Amazon or Facebook, a cookie did that. Many browsers these days, even Google Chrome, block third party cookies, but this may not be a perfect solution. Malicious websites might embed content from a social media site like Facebook to try and trick your web browser into connecting to that service, and possibly giving them access to the cookies in your browser related to that service. For that reason, if you are going to visit any website that you don’t totally trust, it would be a good idea to do it in a private window to prevent any malicious content on that site from trying to access personal information that might be stored in your regular browsing session.
All that being said, it’s important to remember that all the protections of these private modes only affect what happens on your device; what files sites can access, whether your history is saved, etc. It does not stop your browser vendor from collecting data about what you do in these sessions and using it for their own purposes, such as targeting advertisements to you. It also doesn’t stop your internet service provider from seeing what websites you visit, nor does it stop the sites you visit from being able to see your public IP address, and therefore, your approximate physical location. If you would like to protect yourself in these areas, here are some things you can layer on top of private browsing modes to solve these issues if you want.

Prevent Browser Vendor Tracking
Honestly, this just comes down to choosing a company that you trust not to be terrible people. If you are concerned about somebody like Google or Microsoft collecting data on your browsing habits, then perhaps you should consider just not using Google Chrome or Microsoft Edge, and instead use Mozilla Firefox, or one of the many Chromium/Firefox spinoffs like Brave, LibreWolf, Vivaldi, etc. One key thing I look for when picking a browser is to make sure that it is “open source”. This means that the program code that makes up the browser is publicly accessible. You don’t have to be a programmer yourself to benefit from this. If the source code is public, that means that it is being regularly inspected and audited by all kinds of people who aren’t necessarily part of the organization that makes the browser. If something is proprietary, that means that the only people who have access to the code is the people who make the browser, so there’s no way of knowing what’s “really” going on under the hood; whether there are intentional back doors, etc. From web browsers to the operating system I use on my laptop, if something isn’t open source, it’s usually an immediate red flag for me.
I can’t tell you what to pick. There are plenty of great options available that cater to all kinds of use cases. There’s even a “gaming” oriented browser called Opera GX. I myself have switched browsers many times over the years. What I can tell you is that right now I personally use Firefox, albeit with several addons and changes made to its default setup.

Prevent Sites from Seeing Your Location / Prevent Spying by Your ISP
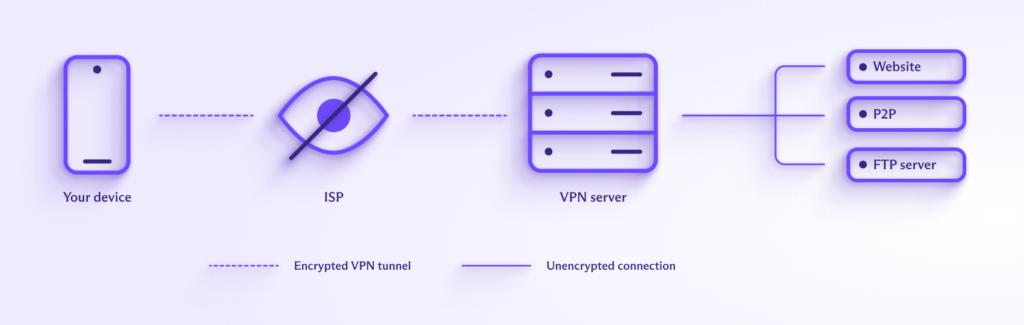
If you are concerned with preventing websites you visit from seeing your physical location, or you want to prevent your internet service provider from seeing your activity, the best solution is a VPN. A VPN is not a magic bullet that will prevent you from catching malware or anything. What a VPN “does” do is create an encrypted tunnel between you and one of their servers. This accomplishes a few things:
- Websites you visit will see the IP address of your VPN provider’s server. Therefore, they will not see your real physical location.
- Your local ISP, that you physically go through for internet access, will not be able to see what websites you visit.
- Other people on your network will not be able to snoop on your activities. They will see that you are using a VPN and that’s it.
Like I said though, using a VPN is not a bullet proof solution. If you visit shadysite(.)org and download sexyladies(.)exe and run it, it won’t matter that you used a VPN to get there. Using a VPN also doesn’t mean that nobody can see what sites you are visiting. Your VPN provider will still be able to see what sites you’re visiting even if your regular internet service provider can’t. You’re essentially just moving the goal posts in terms of who you are choosing to trust. If you feel like you can’t trust your ISP not to snoop on your lawful internet traffic, or not to restrict your access to certain types of lawful content, then a VPN can circumvent them. A VPN might also be useful if you have to use public internet, like unencrypted WiFi at an airport or something. Besides routing your traffic through a VPN server in terms of location, that route or “tunnel” is encrypted, which means nefarious actors on that public network won’t be able to see what you’re doing. They will know you are using a VPN, but that’s it.
One thing to remember though is that not all VPN providers are created equal. Like Incognito mode, many VPN providers blatantly overstate the capabilities of their service, and some of them lie outright about what their service actually does. It would be easy to actually end up worse off than if you had just not used one at all. I personally use a paid subscription to ProtonVPN, and there are other trustworthy providers like Mullvad, but this is a whole can of worms I’d rather not get into here, perhaps in a future article. I just want to suggest that, when choosing a VPN, do plenty of research, and avoid free VPNs. Some services, like Proton, have a paid tier that essentially subsidizes the slower, less flexible free accounts, but many “free” VPN companies have been found collecting and selling data on their users, which makes sense when you think about it. Running a service likes that has regular, recurring expenses, and if you’re not paying them for the service with money, you’re almost certainly paying them with your data.

Protect Yourself from Viruses or Malware While Browsing
There are a few different things you can do to protect yourself from computer viruses or malware while using a web browser.
The first and most important thing is to make sure that your web browser and your operating system (Android, Windows, macOS, iOS, Linux, etc.) are all up to date. New threats or vulnerabilities are found daily, so it’s important to keep the things you use updated so that they know how to defend against those issues.
Another way to protect yourself is just to use common sense. Don’t click suspicious or unsolicited links you get in an email, don’t visit shady websites you’re not sure about, even in private browsing mode, etc.
Another huge thing you can do is to install an ad blocker. There are a variety of stand alone web browsers like Brave or Vivaldi that can block ads out of the box. Other browsers, like Firefox and Chrome, can use addons like uBlock Origin or AdBlock Plus to block ads, but those addons have to be installed after the fact. Some VPN providers even have options to block ads for your whole device while you’re connected to their VPN.
Even the FBI has recommended in the past that people use ad blockers. Websites earn money thru ad revenue. The way it should work is that some company gets paid to place an ad in a spot on their website. When you visit that website, you see the ad and they get paid for the visibility. However, the internet today is far from perfect. Many websites are so inundated with intrusive ads that they’re basically unusable without an ad blocker, and many websites don’t post the ads themselves, so there’s sometimes little to no oversight for what actually gets displayed in those ad spots. Website owners will embed a link to a particular address that an advertiser has control of, and then the advertiser controls what actually exists at that link. This means that when you visit the site, your web browser is actually downloading information from a third party you have no knowledge or control of, and sometimes that content is malicious in nature, without the owner of the site you visited even knowing. So you could visit a totally legitimate website and become compromised because of a malicious advertisement placed somewhere on it. This is “malvertising”, taking advantage of advertising space to trick people into downloading malicious content onto their device, sometimes without their knowledge.
Source – Even the FBI says you should use an ad blocker – TechCrunch
As a last resort, you can also use an antivirus or other security solution on your device so that if you contract some digital nasties, hopefully it will spot and eliminate them. If you’re on a modern Windows system, honestly I would suggest you just stick with the built-in Windows Defender. It performs reasonably well in tests and doesn’t have much of an impact on the performance of your PC. Many other solutions will try to upsell you on upgraded versions of their “advanced security suite” or “total 360 protection” or whatever, and most of it is predatory nonsense designed to juice money out of people who don’t know any better. macOS has a multi-layered approach to check the authenticity of software you try to run, scan for malware, etc. Linux users can optionally install and use ClamAV to scan for malware. I call antivirus a “last resort” however because it’s best to act responsibly and avoid infection in the first place. Malware and viruses are often contracted because of bad OPSEC, or “Operational Security”. You can pay all the money in the world for security theater, but if you click a phishing link and give your login credentials to a fraudulent website, or if somebody uses malvertising to compromise your web browser and collect information from the cookies it has stored, it isn’t going to matter. That isn’t to say that security software is pointless, but don’t feel pressured to go out and spend a bunch of money on something that won’t be any better than the stuff that comes free with your operating system. If anything, aftermarket security solutions will usually make your device run slower because of all the unnecessary bloat they come with. At the end of the day, the best antivirus in the world is you and your ability to act responsibly online.

Conclusion
So to summarize, “private browsing” or “incognito” modes are one of many tools you have in your toolbox to stay safe online. They create temporary/ephemeral browsing sessions that can be useful when you don’t want your activity in that session to be stored permanently on that device. However, they have sometimes been marketed dishonestly as some kind of super secret squirrel security solution, when that’s not at all what they are. It’s important that people understand what a tool is useful for and what its limitations are, or they might behave irresponsibly in a situation where they thought they were safe and protected, and were in fact not.
Shameless Personal Plug
Writing blogs like this takes time and effort. If you have found value in my work or if it has benefited you in any way, I would appreciate it if you would consider donating to help compensate me for my time. There are several ways you can do this, so here they are in no particular order.
PayPal: https://paypal.me/gerowen
LiberaPay: https://liberapay.com/gerowen
Bitcoin (BTC):
bc1q86c5j7wvf6cw78tf8x3szxy5gnxg4gj8mw4sy2

Monero (XMR):
42ho3m9tJsobZwQDsFTk92ENdWAYk2zL8Qp42m7pKmfWE7jzei7Fwrs87MMXUTCVifjZZiStt3E7c5tmYa9qNxAf3MbY7rD


