An OpEd by Marcus Adams. Any opinions stated here do not necessarily reflect the opinions or stance of Magoffin News Network. More information about the author can be found at the bottom.
You think you have nothing to hide? Can I have your social security number? What about your bank account and routing number? The username and password to your Facebook account? Can I look through all the pictures and text messages on your phone?
No matter how mundane you might think your life is, there are parts of it that don’t concern anybody else. It’s none of their business. Privacy isn’t about hiding parts of your life from other people because you’re doing something shady, it’s about controlling what information people have access to, and only letting them into the parts of your life that they actually have a valid reason to be a part of. It’s the reason you’re fine with giving your debit card number to Amazon when you place an online order, but you’re not OK with handing it to some random stranger on the street. It’s about controlling the flow of your information.

Privacy is also about safeguarding your right to free speech. People behave differently when they think they’re being surveilled. They will, sometimes without even realizing it, censor themselves and avoid difficult topics or not express controversial opinions. It’s like being in a perpetual Thanksgiving dinner where you “want” to say something, but you’re afraid to. You shouldn’t feel the need to censor yourself or to behave in a certain way because Amazon might serve you a creepy ad, or “accidentally” send your conversation to a neighbor, or because some NSA agent might be watching you undress.

Privacy is also about protecting your information in the event of a breach of some website or service that you use. If your email provider gets hacked, and the hackers start perusing your emails, will they find anything useful? Will they be able to find your phone number, physical address, card numbers, etc. from emails you’ve gotten from online retailers? Or will those emails be encrypted in a way that protects them from access, even if the provider gets hacked? Some encrypted email providers minimize the access that even they have to your account. This ensures that even when (not if) they are breached, the threat to your personal information is minimized because all of your data is encrypted. Some providers however, like GMail, have full, unfettered access to your emails and everything in them. They scan the contents of those messages to serve you ads and build a profile on you. This means that if that service is hacked, your emails essentially become public record.
To be clear, there are situations where the police may have a legitimate need to know what you’re talking about, and in those situations, police can issue a warrant or a court order to seize your devices and even compel you to unlock them. If a pedophile uses an encrypted messaging service to coordinate their activities, the police have the power to seize their devices and collect evidence from those devices. Advocating for privacy doesn’t automatically mean you want to protect criminals’ ability to carry out malicious acts. It means protecting the right of people to think, speak and exist online without unwanted intrusions into their life. Contrary to what many politicians want you to think, encryption isn’t a danger to children. Encryption is the one thing in this world that forces them to protect your 4th amendment rights because they don’t have a choice, and in the post 9/11 era of things like FISA courts and the patriot act, not being able to spy on all people, all the time, runs contrary to their goal of total surveillance of the entire population.
This is why, in my opinion, it’s important to use products and services that respect your privacy. I understand that while I may host my own Nextcloud and other services, that level of involvement is not reasonable to expect from most people. But what you can do is do your best to research and choose products and services that have been proven to respect your privacy.
Below, I will discuss a few of the options and why I think they’re valuable to consider. This is not an exhaustive list of every product that I consider trustworthy, but it’s products that I either personally use, have helped others use, or that I wouldn’t have any problem with recommending or using myself. My goal here isn’t to convert everybody to everything that I use, it’s to let you know that there are private options available for a lot of things. It’s up to you to develop your threat model and implement whatever solutions you think fit that model.
Messengers
Instant messaging is probably the primary way we all communicate these days. Therefore, in my opinion, it’s the one change you could make that would offer the biggest impact on your privacy. The most ubiquitous, at least with many of the people in my life, is Facebook Messenger, which is one of the worst products you can use for your instant messaging. Meta is rolling out end-to-end encryption right now, but it’s still a proprietary black box that can’t be audited by objective third parties, and I have personally caught Facebook systems browsing file shares that I sent to individuals via Messenger, months after I sent the link and credentials out. I have basically two criteria for even considering an instant messaging service. It must be open source, and it must be end-to-end encrypted, or at least have the option to turn on end-to-end encryption. Here are some of my recommendations.
Signal

Signal is an end-to-end encrypted messaging service. It’s my default messaging service of choice because it’s simple, proven secure and quick to get set up with. Their encryption protocol is the gold standard and has been implemented in many other products. They even recently updated their encryption to resist attacks by quantum computers. It has been subpoenaed multiple times by the FBI and proven in court that even under subpoena, the only information they can provide is:
- When you registered for the service.
- The last time you signed in
They can’t reveal who you talk to, what you said, your location or anything else. ”End-to-end encryption” means that once your message leaves your device, nobody in the middle can read or alter it. However, this does not protect your messages from being read on your device, so if somebody gains physical access to your phone (such as police with a warrant), or if your phone has malware (viruses, etc.) on it, your messages can potentially still be read on your device, or the device of the person you’re talking to.
The one down-side to Signal is that it requires a phone number to sign up, and even the desktop application has to be “linked” to a mobile app. That means that in order to use Signal for secure communications with somebody, you have to give them your phone number and use the mobile app to “link” the desktop app on your PCs. You can get around this by using a VOIP number from Google Voice or something, but it’s something to consider.
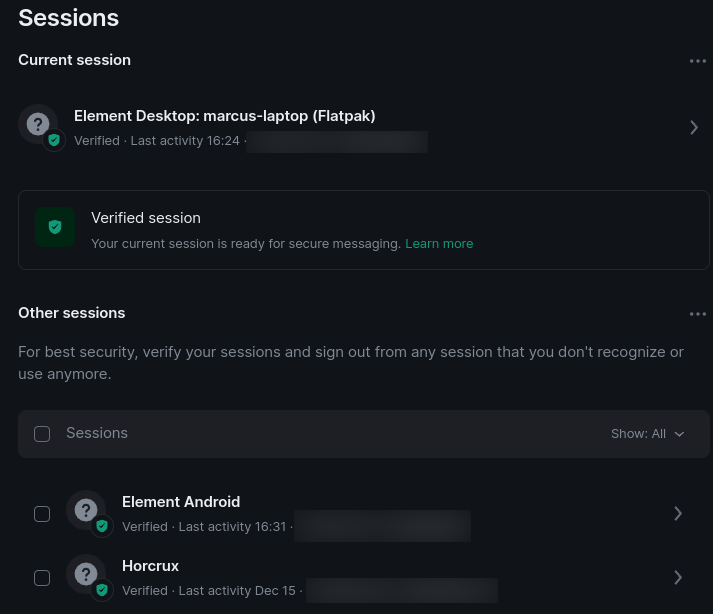
Signal also has the ability to view and control which devices have access to your account, so that you can verify whether an old or otherwise unauthorized devices can read your messages, and revoke that access.
Session

Session is an end-to-end encrypted messenger that started out as a fork of Signal. It’s a bit more technical to use (though only a bit), but it has two main advantages in my opinion.
- It doesn’t require a phone number. Instead, when you create an “account”, it basically just gives you a seed phrase that serves as your password to set up other devices, and an “ID” that you share with other people you want to talk to. This ID is not tied to you personally in any way, and if you ever feel that your ID has been compromised for any reason, you can just create another one on the fly because it’s not tied to your phone number or any other aspect of your real identity.
- It doesn’t have a centralized server. It runs on a decentralized, peer-to-peer network. As of writing this has some limitations and drawbacks. For example, video/voice calling still establishes a direct connection between you and the other person, which exposes your IP address, and regular text messages can sometimes take a moment longer to send, since they’re being routed through multiple hops.
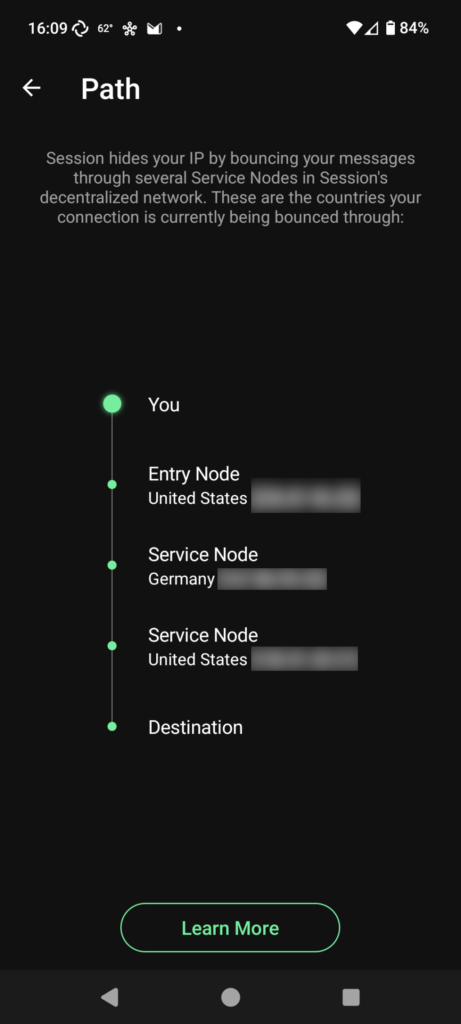
Unlike Signal, and due to its decentralized nature, Session does not have an option to view which devices currently have access to your “account”, so it’s vital that you make certain to safeguard your seed phrase so that nobody is able to connect a device to your ID and read your messages without your knowledge.
Element

Element is a messenger built on the “Matrix” protocol. In fact, Element is just one of many messengers you can choose to use on Matrix, but Element is developed by the same folks who are developing Matrix, so it’s an easy default option. Think of Matrix like e-mail. Just like anybody can host their own email service and then send and receive emails with anybody else, anybody can host their own Matrix server and then exchange messages with anybody else. Just like a GMail user can send emails to somebody on Outlook, somebody on matrix(.)org can exchange messages with people on any other Matrix server.
One-on-one messages in Element are end-to-end encrypted. Group chats in Element can also be end-to-end encrypted, but may not always be. Admins of that room may choose to turn it off, or the room may be bridged with an external service so that encryption isn’t possible. So if you’re concerned about the privacy of a group conversation, look for the little shield icon at the top.
Element, like Signal, also allows you to verify which devices currently have access to your account, and to revoke access to old devices.
One cool feature of Element/Matrix is that there are lots of chat rooms or group chats. If you’ve ever used Discord or Telegram to connect with a community, it works a lot like that. Session, mentioned above, also supports communities, but they’re not nearly as fleshed out or widely used as the Matrix “Rooms” are.

EMail is one of the oldest, and most distributed forms of online communication. It’s often said that it was never intended to be private because the internet was a very different place when the protocols that power e-mail were ratified and put into practice. Nowadays, however, email providers regularly scan your emails for any information they find valuable. When I did a Google Takeout years back I found that Google had been parsing my emails and storing data about all my online purchases from places like Amazon. They knew what I bought, the link to the product page, how much I paid, where I had it shipped to, etc. Yahoo! was hacked in 2013, resulting in the compromise of every single user. Since Yahoo! doesn’t encrypt data at rest, that means that every email stored in all 3 BILLION of those accounts was just laid out there for anybody to read. EMail encryption has been a thing for decades, but unless you were a company or government organization, basically nobody actually implemented it, and certainly none of the free email providers bothered with it. In recent years however, a handful of services have sought to rectify the issues with email. Here’s my thoughts on them.
ProtonMail

ProtonMail is my email provider of choice. I pay for a family plan for myself, wife and kids. Proton uses, supports and further develops the OpenPGP standard. This means that not only are emails sent between ProtonMail users end-to-end encrypted, it means that you can send encrypted emails to anybody on any service who takes the time to set up their own PGP keys and use them. Obviously you can also email anybody on any other service without bothering with the encryption.
ProtonMail has a free plan, as well as paid family and business plans.
Encrypting email is a little more difficult, because there’s a variety of different providers, most of whom (like GMail), offer no encryption or protection whatsoever of your data after it’s on their servers. But, here’s what ProtonMail offers:
- Industry standard PGP/GPG end-to-end encryption. This means that all emails between Proton users are automatically encrypted end to end, but it also means that you can exchange an encrypted email with anybody on any service, including GMail, if they set up their own PGP keys.
- “Zero access” encryption of your data at rest. Basically this means that nobody, not even Proton, can access the data in your account without your password. This means that Proton can’t read your emails, and if they’re ever breached, your emails and other data will be safe because not even Proton has access to it.
- “Password protected” emails with optional expiration dates. If you need to use email to send some sensitive information to somebody who uses an unsafe service like Yahoo, Outlook or GMail, you can password protect the message, then just call them or send them a message on Signal or something with the password. The recipient will receive a link that allows them to decrypt and open the message when the password is entered.
- Support for securely storing your contacts and calendar.
Tuta (Formerly Tutanota)
Tuta has many of the same privacy benefits as ProtonMail, but the way they achieve that is different. While ProtonMail uses standard PGP/GPG, Tuta uses their own encryption scheme. Tuta, like ProtonMail, can exchange regular emails with anybody on any other service. Here are some of the things Tuta offers.
- Automatically end-to-end encrypted emails between Tuta users. Since they don’t use PGP/GPG, it’s not, as far as I’m aware, possible to receive encrypted emails from external services.
- “Zero access” encryption of your data at rest. Your data is encrypted at rest on their servers, which means that not only can Tuta not access your data, it means that if they’re breached, the hackers won’t be able to access it either.
- “Password protected” emails for sending sensitive emails to recipients on unsafe services like GMail, Yahoo or Outlook. You can password protect a message, then share the password with the recipient by calling them or sending it using some other out of band method, and then rest assured that the recipient’s email provider, or hackers of that service at some later date, won’t have access to the contents of the message.
- Support for securely storing your contacts and calendar.
File Storage
Most of the big cloud storage providers are far from private; they have complete access to anything and everything you upload. I discovered years ago that every image in my Google Photos, including ones I had never shared, had a web address assigned to it that could be used to access it publicly with no authentication. Folks like Microsoft and Google aren’t shy about admitting that they regularly scan your files for anything they deem questionable or wrong-think. A father was recently flagged as a criminal by Google when he took nude photos of his son to send to the doctor. After a 10 month criminal investigation and police officially stating that “no crime had been committed”, Google still refused to reinstate the man’s account and informed him it would be permanently deleted. This affects his whole Google account; GMail, drive, maps, photos, any Android apps or music he’s paid for in the Play Store, everything, all because he trusted Google to back up his photos without being creepy.
Here are some more privacy respecting alternatives.
Proton Drive

Created by the same folks as ProtonMail, Proton Drive is an encrypted file storage solution. Like their email product, your data is encrypted at rest so that if they’re breached, the hackers will only be able to access encrypted, and therefore unreadable, copies of your data.
Proton Drive is a fairly new product, so it’s missing some features that other services like Microsoft OneDrive or Google Drive may offer. Here’s what they do offer though, as of writing:
- A web interface where you can upload, download and share files.
- Apps for Android, iOS, Windows and Mac OS. The mobile app allows you to sync your photos automatically.
Cryptomator

Cryptomator is actually not a cloud backup service in and of itself. What cryptomator does is allow you to encrypt your files locally, and then sync the encrypted copies to the cloud storage solution of your choice. What you do is you create an encrypted “vault” on your device, and then store files within that vault. You can then sync that vault to any cloud storage service. The owner of the service can’t see inside your vault and you get to continue using a service that you may already be paying for.
Cryptomator has apps for Windows, macOS, Linux, Android and iOS. It’s free to use on desktop operating systems, but the mobile apps, at the time of writing, have a one time fee of $10-$15.
BackBlaze

Backblaze is not really a “cloud storage” solution, it’s more of a “backup” solution intended for disaster recovery. One of their products is just called “Computer Backup”. For $9 a month (at the time of writing) you can get unlimited, encrypted backup of your PC or Mac. If you need to restore those files, you can either download them, or for an extra fee they will even mail you a hard drive with your files on it. A desktop application stays running in the background of your desktop PC and keeps your local files backed up to the service in real time.

They also have mobile apps that you can use to browse the files backed up by your desktop computer.
Nextcloud

Nextcloud is a technical option, and is definitely not for everybody. Nextcloud is an open source cloud storage solution that you can self-host, and it’s the one I use. I physically own and operate my own server here at home that runs Nextcloud. You can also purchase space on others’ Nextcloud servers, though none of those are “official”; they are companies or maybe even regular folks like me who choose to sell space on their servers. The amount of privacy you get from those servers can be great, or worse than what you get from Google, just depending on the policies of the person hosting the server and how their server is configured.

Nextcloud advertises “certified” providers, but they are still folks hosting their own service and are unaffiliated with Nextcloud and their company, so they have the above disclaimer on that page. Whether or who you trust when signing up is up to you. Nextcloud does have an “encryption” option that can be enabled, so one thing to look for is whether they’ve enabled that. If they haven’t, then that means the server administrator has access to your files.
But, I wanted to mention it because it is an option, and if you are tech savvy enough to host it yourself, and don’t mind the work that is involved with maintaining the server, proper backups, etc, you can’t get much more private than hosting your own cloud storage.
Extras
These are some other misc. products and services that I use, so I thought I would throw them onto the end and explain what they are and why I find them valuable.
SimpleLogin

SimpleLogin is an email aliasing service. There are other services like Mozilla relay ran by the same folks who make the Firefox web browser and a handful of others, but as a paying customer of ProtonMail, I also get access to SimpleLogin, so that’s the one I use. If you are not a paying customer of ProtonMail, feel free to check out Mozilla relay, Mysudo or other services that offer email aliases.
EMail aliases are exactly what they sound like. You generate an alias that you can use for a specific business or category, and then give that email address out. Emails sent to that alias get forwarded to your real email inbox, without you having to give your real email address out to everybody who asks and getting flooded with spam in a year or two.
Here’s an example. Tonight I did some shopping at Ollie’s, and was asked if I wanted to get a rewards card. I agreed, but instead of giving them my real email address, I opened the SimpleLogin mobile app on my phone, generated an alias just for them and gave them that. If they start spamming the daylights out of me, I can just turn that alias off and close the floodgates, without them having my real personal email address that’s more difficult to change. You can even reply and send emails back to that address, and from the perspective of the recipient it will appear that the email originated from that alias you gave them.
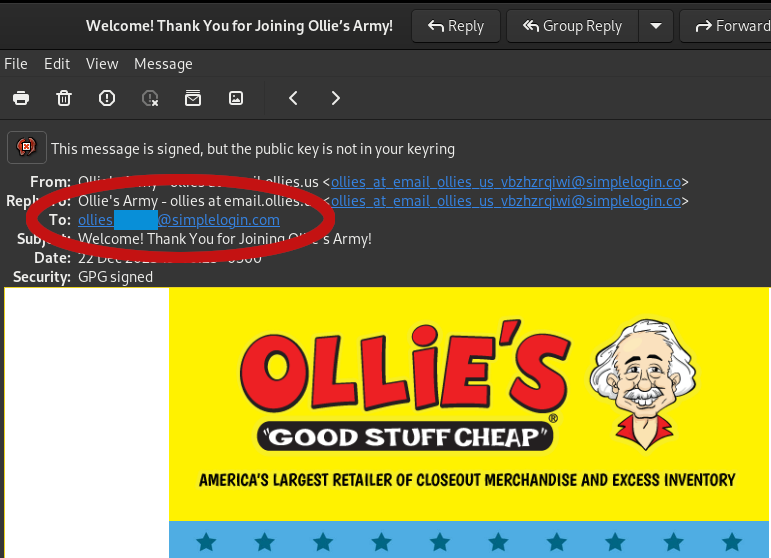
Note that some online services may block the use of email aliasing services like this. It’s not common, but it does happen. If that happens, most email providers allow you to create basically infinite aliases with a + symbol added like name+service@email.com . So for example, if your email address is joe@gmail.com and you wanted to create an alias for Ollie’s, you can just tell them to use joe+ollies@gmail.com . You don’t even have to set these up ahead of time unlike SimpleLogin. The one down side to these is that any human looking at it can tell that your real address is just joe@gmail.com, but they should help control automated spam emails and let you know where the junk is coming from by creating rules based on that alias if you start getting spam.
Privacy(.)com

Privacy does for debit/credit cards, what SimpleLogin does for emails. Mysudo is another service that offers similar functionality, but Privacy was the first one I learned about, so it’s the one I have been using. You can generate virtual cards that are real, functional Visa cards. You then give the details of those cards to online vendors in lieu of your real card. Then, if that vendor ever gets hacked, they try to double charge you, renew a subscription without your permission, etc., you can just go turn off that one card instead of canceling your real debit/credit card and waiting several days to get a replacement in the mail. Privacy also allows you to set individual spending limits for each card, you can create one time use cards that turn off after the first transaction, etc. Whether it’s Amazon or a paid parking lot, Privacy(.)com makes it super simple to transact securely without potentially compromising your real card.

Google Voice

There are a variety of VOIP services that let you register a real phone number and place regular phone calls. Skype, Google Voice, Mysudo, etc. all do this. I don’t make as much use of this as some other people might, but I do have a number registered with Google Voice and any time somebody might need to call me, but I’m not comfortable giving them my real number, I give them my Google Voice number. It lets you make and receive calls, often for free, registering and keeping the number is free, it supports storing voicemails, etc. And if somebody starts spamming me I can very easily just change the number without affecting my real cell phone number.
AT&T ActiveArmor

This is a mobile app that is specific to my cell phone carrier. It’s in Google Play (and presumably iTunes), so anybody can install it, but it probably wouldn’t work on non-AT&T devices. Other carriers may have comparable products, or there may even be third party products that accomplish the same goal, but this is the one I use.
AT&T ActiveArmor is many things. One feature it has is an antivirus that will scan your phone for known malware. The feature I make the most use of however is the ability to control incoming calls at the carrier level. Most of us are familiar with the little red notice that will pop up when you receive a call that says “Suspected Spam” or something to that effect. What ActiveArmor does is apply these controls at the carrier level and let you customize what happens to different types of calls. For example, I have mine set so that unknown callers get sent straight to voicemail. So if you’re a private caller, or you’re not in my contacts list, it won’t even ring through in the first place.
This app has been invaluable because it helps me control what calls my kids actually receive on their phones, so I don’t have to worry about strangers calling them, and none of us have received any spam or telemarketing calls since we started using this app.
If you’re an AT&T customer, I highly recommend you check out the AT&T ActiveArmor mobile app.
Conclusion
There’s a lot of things you can do, in many areas of your life, to increase your privacy. Whether or not you’re ready to ditch Facebook or GMail entirely is not for me to decide. However, I just wanted to take some time to outline some of the things that I use to protect the privacy of myself and my family online so that if you’re just starting your privacy journey, maybe I will have brought some things to your attention or planted some ideas for you to explore. The important thing is that you know there are options so that when you’re developing your threat model and deciding what areas need improvement, you can make and execute a plan to achieve your desired results.
It’s like I said at the beginning, privacy online isn’t about staying totally anonymous all the time or about protecting criminals, it’s about protecting the flow of information and safeguarding your personal details in the event of a breach. No matter how mundane you might think your life is, there are things about you on your devices, and elsewhere on the internet for that matter, that don’t concern anybody else, and could be used against you by bad actors, so it’s important that you understand how to protect yourself and not give out unnecessary personal details in a world that is becoming increasingly dependent on the internet.
Shameless Personal Plug
You can read this and other blogs by me at my personal WordPress page, or you can follow me on Mastodon. I also have a Facebook page where I post tech news and advice.
Personal WordPress: https://gerowen.wordpress.com
Facebook Page (Marcus’s Tech News and Advice): https://www.facebook.com/profile.php?id=100089830885315
Mastodon Profile: https://mastodon.social/@gerowen
Writing blogs like this takes time and effort. If you have found value in my work or if it has benefited you in any way, I would appreciate it if you would consider donating to help compensate me for my time. There are several ways you can do this, so here they are in no particular order.
PayPal: https://paypal.me/gerowen
LiberaPay: https://liberapay.com/gerowen
Bitcoin (BTC):
bc1q86c5j7wvf6cw78tf8x3szxy5gnxg4gj8mw4sy2

Monero (XMR):
42ho3m9tJsobZwQDsFTk92ENdWAYk2zL8Qp42m7pKmfWE7jzei7Fwrs87MMXUTCVifjZZiStt3E7c5tmYa9qNxAf3MbY7rD

